Try Hack Me - Crack the hash
Howdy my fellow Cyber Enthusiasts! Let's crack some hashes. This guide is for Linux users, these commands will not work for Windows. You can always use Attackbox from Try Hack Me, which will open a Linux Machine accessible from the web browser.
Can you complete the level 1 tasks by cracking the hashes?
48bb6e862e54f2a795ffc4e541caed4dThis is a MD5 hash. The MD5 message-digest algorithm is a widely used hash function producing a 128-bit hash value. Let's look at the following examples below. Imagine we are going to create a .txt file called root.txt and pass the following contents into it.
root.txt
Hello MD5!Now, use the following command.
md5sum root.txtYou will get a unique value like the below. This is like a identifier that specifies that file. If you've created another file with different content, you will get a different hash value.
65b95813030b652a6a9cd24b00809a6e root.txtNow, for this room, use the following command to write the MD5 hash into a file called crack.hash
echo "48bb6e862e54f2a795ffc4e541caed4d" > crack.hashNow, we will use john in order to find a possible match for the MD5. If you are using Kali Linux, it is likely that you will have this tool installed. If you don't, use the following command.
sudo apt-get install johnNow, we need to install our wordlist to decrypt the hash. We will the most common wordlist, rockyou.txt. Use the following command to download it to your computer.
wget https://github.com/teamstealthsec/wordlists/raw/refs/heads/master/rockyou.txt.gzTo unzip the wordlist use the following command. Install the tool if necessary.
gunzip rockyou.txt.gzNow, we are almost ready. Just replace the path of the rockyou wordlist with yours.
john --format=raw-md5 crack.hash --wordlist=/usr/share/wordlists/rockyou.txtNice job! You found the first answer.
Let's proceed with the next task.
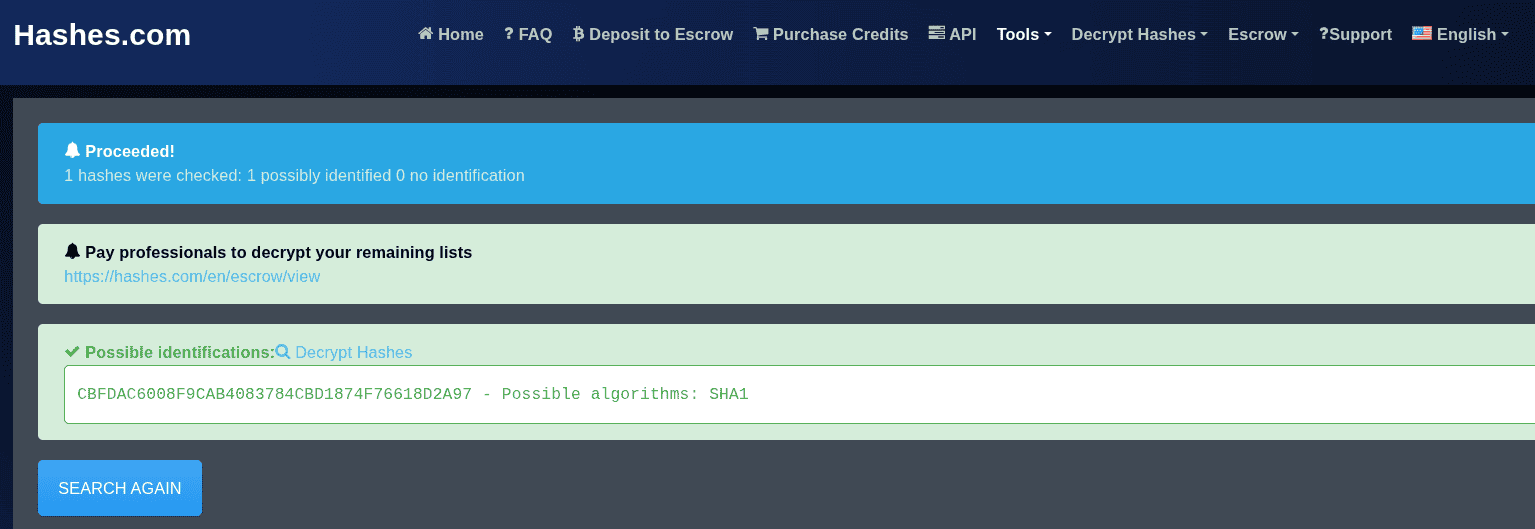
CBFDAC6008F9CAB4083784CBD1874F76618D2A97Again, write the hash to a file.
echo "CBFDAC6008F9CAB4083784CBD1874F76618D2A97" > crack2.hashWe follow the same approach as before, but the hash is changed from MD5 to SHA1. You can find the hash identifier by using this website.
john --format=raw-sha1 crack2.hash --wordlist=/usr/share/wordlists/rockyou.txtIf the hash is cracked, and you run the command again the password won't be shown. For that use the following command.
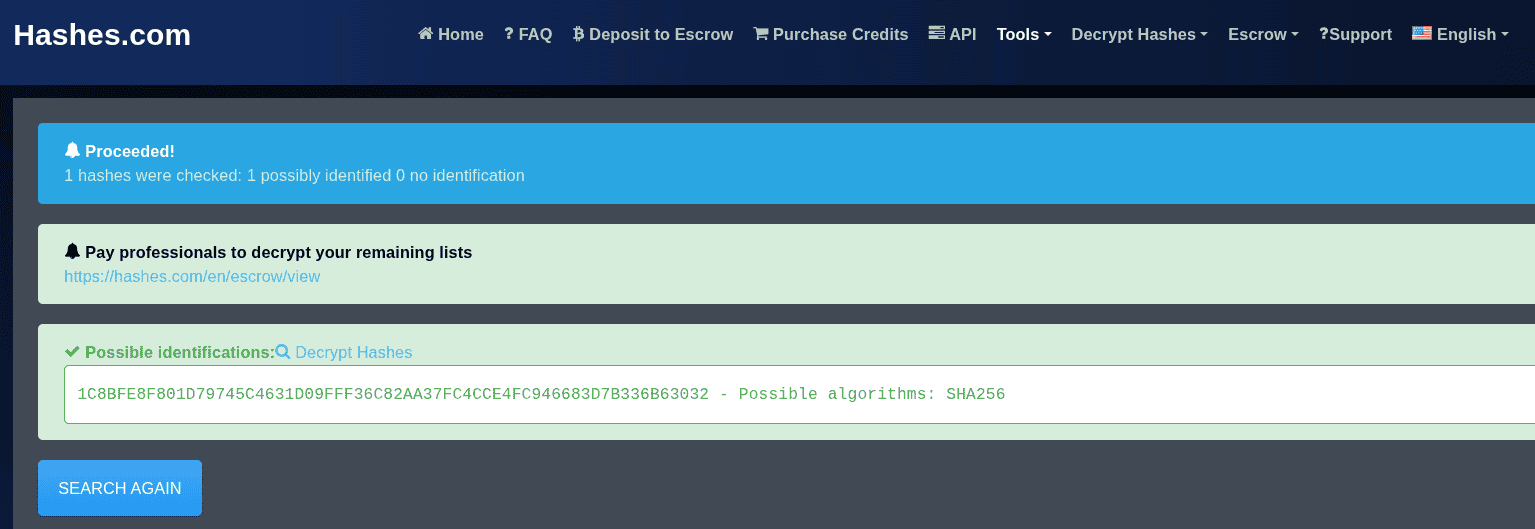
john --show --format=raw-sha1 crack2.hash1C8BFE8F801D79745C4631D09FFF36C82AA37FC4CCE4FC946683D7B336B63032Write the hash to a file.
echo "1C8BFE8F801D79745C4631D09FFF36C82AA37FC4CCE4FC946683D7B336B63032" > crack3.hashAgain, visit the previous website to identify the hash type.
john --format=raw-sha256 crack3.hash --wordlist=/usr/share/wordlists/rockyou.txt$2y$12$Dwt1BZj6pcyc3Dy1FWZ5ieeUznr71EeNkJkUlypTsgbX1H68wsRomecho '$2y$12$Dwt1BZj6pcyc3Dy1FWZ5ieeUznr71EeNkJkUlypTsgbX1H68wsRom' > crack4.hashAgain, visit the previous website to identify the hash type.
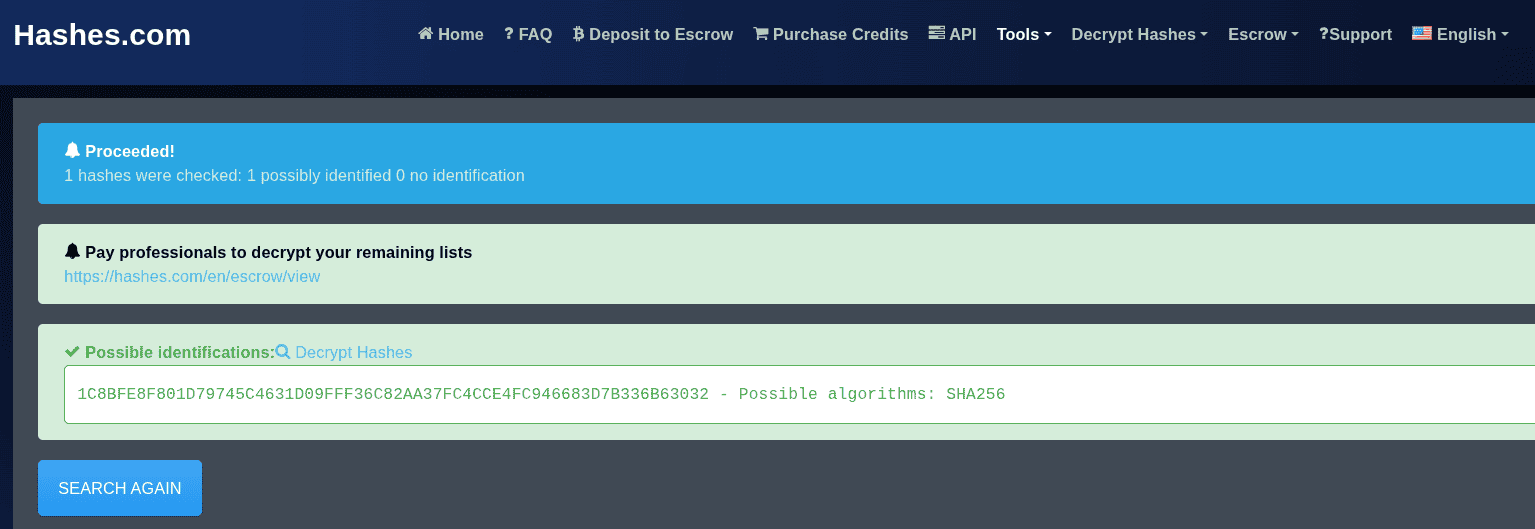
Since, this hash is more complex than the previous ones, I will give one hint for this, as you can see from the THM website.
This is the hint you’re looking for: Search the hashcat examples page (https://hashcat.net/wiki/doku.php?id=example_hashes) for $2y$. This type of hash can take a very long time to crack, so either filter rockyou for four character words, or use a mask for four lower case alphabetical characters.The following command looks the entire rockyou.txt file and keeps only the 4 lowercase strings and passes the output to a file called 4lower.txt
grep -E '^[a-z]{4}$' /usr/share/wordlists/rockyou.txt > 4lower.txtjohn --format=bcrypt crack4.hash --wordlist=4lower.txt279412f945939ba78ce0758d3fd83daaThis is a MD4 hash, provided by the hint or from the website we saw earlier multiple times.
echo "279412f945939ba78ce0758d3fd83daa" > crack5.hashjohn --format=raw-md4 crack5.hash --wordlist=/usr/share/wordlists/rockyou.txthashcat -m 900 crack5.hash /usr/share/wordlists/rockyou.txtWe've run these commands, but still no response. That means no result was found, which means the password is not present in rockyou.txt. We can try another list, and we might get lucky, but for the purpose of this post, we will explore other options.
Source 1:

Source 2:

Source 3:
Just paste the hash and you will get the answer! 😄
Hash: F09EDCB1FCEFC6DFB23DC3505A882655FF77375ED8AA2D1C13F640FCCC2D0C85Use the following website to find the hash identifier.
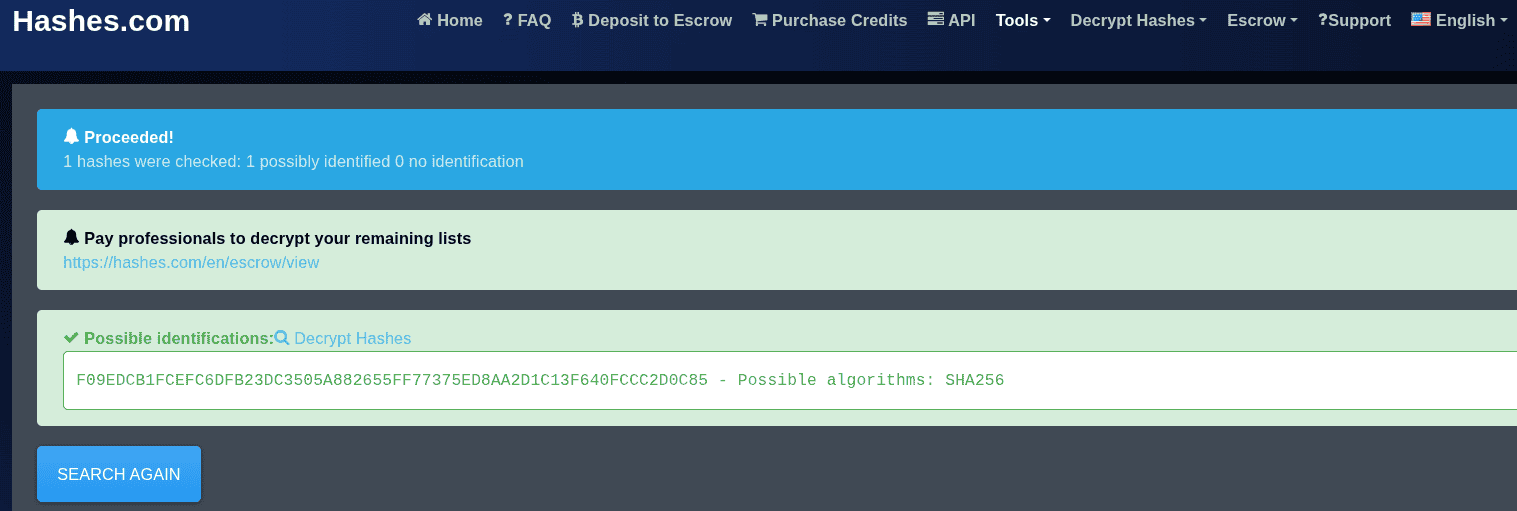
echo "F09EDCB1FCEFC6DFB23DC3505A882655FF77375ED8AA2D1C13F640FCCC2D0C85" > crack6.hashNow, let's use hashcat to find the answer.
hashcat -m 1400 crack6.hash /usr/share/wordlists/rockyou.txtHash: 1DFECA0C002AE40B8619ECF94819CC1B echo "1DFECA0C002AE40B8619ECF94819CC1B" > crack7.hashThe hint from THM is NTLM.
NTLM (Windows NT LAN Manager) is a suite of Microsoft security protocols providing authentication, integrity, and confidentiality, primarily used for single sign-on (SSO) in Windows environments. It uses a challenge-response mechanism, where user credentials are hashed rather than sent in plain text, though it is considered legacy and less secure than Kerberos.
We will use hashcat for our case.
hashcat -m 1000 crack7.hash /usr/share/wordlists/rockyou.txtIf you want to find the hash mode (this is the number after -m), you can visit the following website.
Visiting the website, we can see that the hash mode for NTLM is 1000.

Hash: $6$aReallyHardSalt$6WKUTqzq.UQQmrm0p/T7MPpMbGNnzXPMAXi4bJMl9be.cfi3/qxIf.hsGpS41BqMhSrHVXgMpdjS6xeKZAs02.
Salt: aReallyHardSaltecho '$6$aReallyHardSalt$6WKUTqzq.UQQmrm0p/T7MPpMbGNnzXPMAXi4bJMl9be.cfi3/qxIf.hsGpS41BqMhSrHVXgMpdjS6xeKZAs02.' > crack8.hashBy using this website, we identified the possible algorithm.
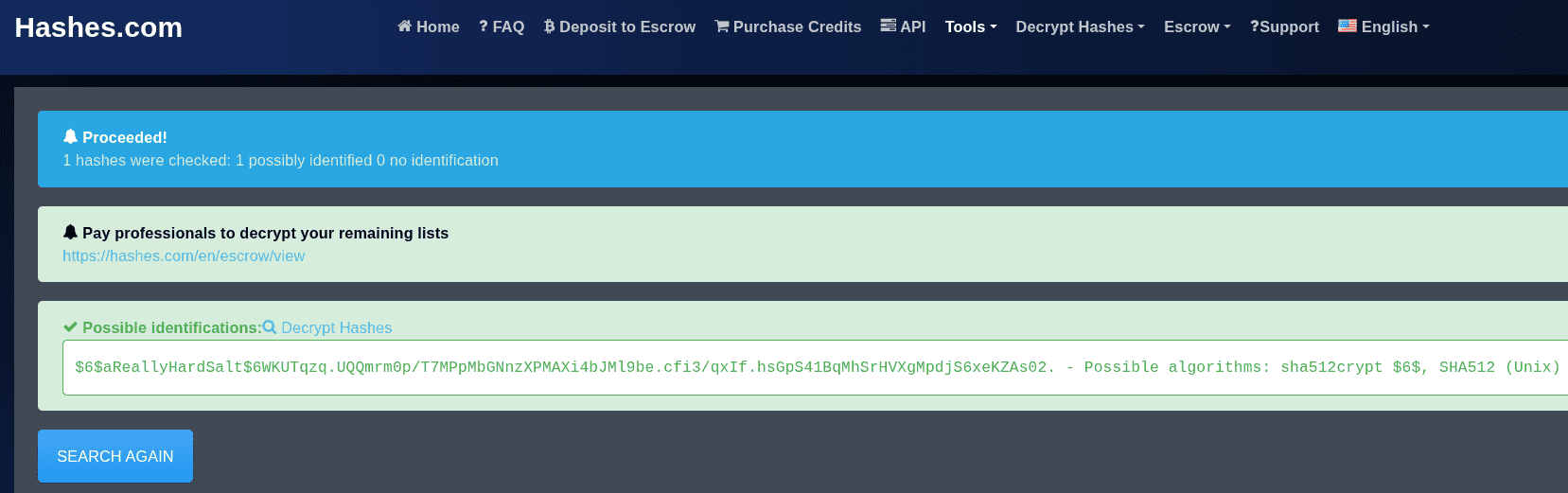
Visiting hashcat.net, we identified the hash mode for our case.

hashcat -m 1800 crack8.hash /usr/share/wordlists/rockyou.txtHash: e5d8870e5bdd26602cab8dbe07a942c8669e56d6
Salt: tryhackmeecho 'e5d8870e5bdd26602cab8dbe07a942c8669e56d6:tryhackme' > crack9.hash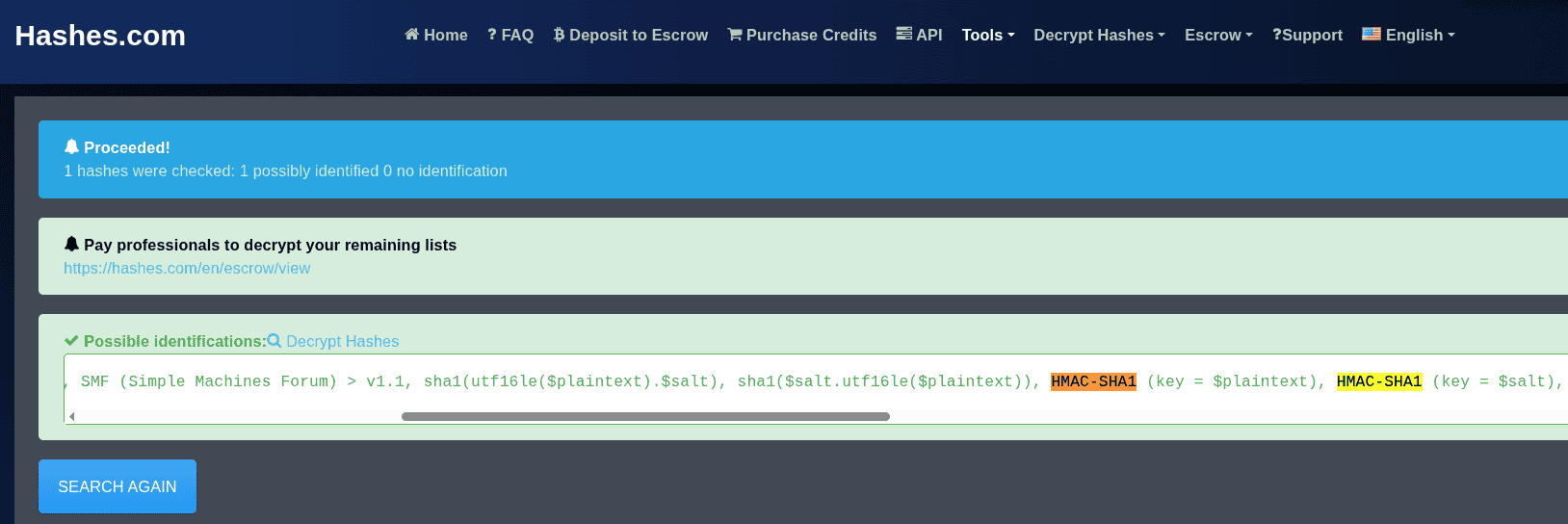
Visiting hashcat.net and searching for HMAC-SHA1 gives the hash-mode 160.
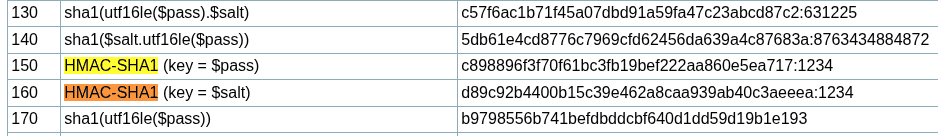
hashcat -m 160 crack9.hash /usr/share/wordlists/rockyou.txtRemember that the hash must be passed as key:salt.
Congratulations! You have solved this room! 🎉 🎉 🎉










